CLOUDBRIK is a turnkey solution for managing all data in the company. A user-friendly management interface (GUI) simplifies management and control. The instant recovery mode ensures uninterrupted work, even in an emergency.
Datenschutz as a Service

CLOUDBRIK allows tiering for data storage.
With CLOUDBRIK, the data is stored in encrypted form in a hyperconvergent infrastructure (HCI). Airgap, media breaks and a WORM functionality protect the data from ransomware attacks. The file system is based on erasure coding. Enterprise search mechanisms ensure that files can be found quickly.
Depending on the use case, the data is stored in one of three available storage tiers:
CLOUDBRIK T1 for backup and disaster recovery
CLOUDBRIK T2 for long-term archiving
CLOUDBRIK T3 as an interface to the cloud
All CLOUDBRIKs are part of Cristie Managed Services. The Cristie Care Packs offer a high degree of flexibility and are available in three SLA variants: Basic, Advanced and Premium. All SLAs can optionally be expanded with the “Plus” package for 7 x 24. From proactive monitoring and reporting to troubleshooting across the entire environment, the Care Packs also include configuration adjustments and support for administrative questions.
Cristie CLOUDBRIK can be deployed anywhere: in your own data center, in branch offices or in multi-cloud environments. Using Cristie CLOUDBRIK significantly reduces the total cost of ownership (TCO), radically simplifies management and protects mission-critical data, including: also from ransomware attacks.
With CLOUDBRIK, the data is stored in encrypted form in a hyperconvergent infrastructure (HCI). Airgap, media breaks and a WORM functionality protect the data from ransomware attacks. The file system is based on erasure coding. Enterprise search mechanisms ensure that files can be found quickly.
Depending on the use case, the data is stored in one of three available storage tiers:
CLOUDBRIK T1 for backup and disaster recovery
CLOUDBRIK T2 for long-term archiving
CLOUDBRIK T3 as an interface to the cloud
All CLOUDBRIKs are part of Cristie Managed Services. The Cristie Care Packs offer a high degree of flexibility and are available in three SLA variants: Basic, Advanced and Premium. All SLAs can optionally be expanded with the “Plus” package for 7 x 24. From proactive monitoring and reporting to troubleshooting across the entire environment, the Care Packs also include configuration adjustments and support for administrative questions.
Cristie CLOUDBRIK can be deployed anywhere: in your own data center, in branch offices or in multi-cloud environments. Using Cristie CLOUDBRIK significantly reduces the total cost of ownership (TCO), radically simplifies management and protects mission-critical data, including: also from ransomware attacks.
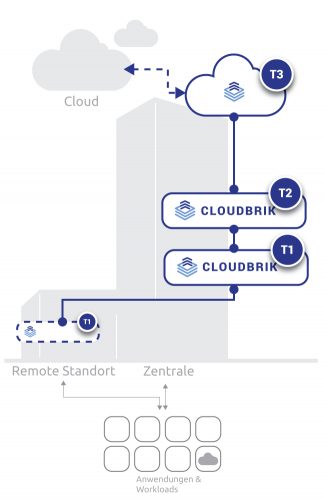
Tier 1: BACKUP & RECOVERY
The TIER 1 CLOUDBRIK is the backup-recovery engine with all the necessary features to protect mission-critical data. The installation takes place on site in the central data center or at a branch or external location.Tier 2: ARCHIVE STORAGE
The Tier 2 Brik was designed to reduce the cost of long-term storage (archival). Erasure coding and a native S3 interface ensure maximum security and reliability. CLOUDBRIK Tier 2 already includes free tiering for CLOUDBRIK T3 (optional public cloud tiering) and can be combined with any S3-compatible application, local storage (on-premises) or custom volumes.Tier 3: CLOUD SERVICES
The third tier is cloud storage, including for more data intelligence and to secure Office365 or other cloud-native applications and services provided as SaaS. CLOUBRIK T3 can optionally transfer data to any other cloud provider (S3).Every CLOUDBRIK is hyper-converged. Based on HCI technology, the appliances consist of 4 servers and are equipped with fast SSDs, powerful HDDs for backup storage and Cristie’s Backup & Recovery software. For operation at remote locations, we recommend using the smaller version CLOUDBRIK AIR.
OPEX statt CAPEX
Each solution is tailored to the individual requirements. In addition to the basic configuration, further functions and services can be added. All CLOUDBRIKs are available as a monthly subscription, with or without upfront payment. The CLOUDBRIK T3 can also store data with a pay-as-you-go option. Of course, combinations of all available billing models are also possible.
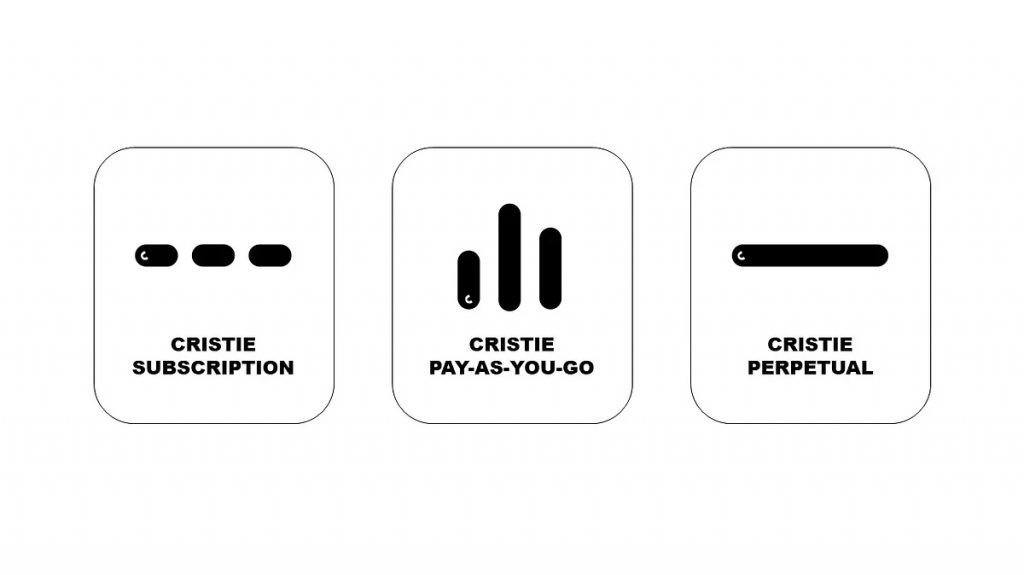
Each CLOUDBRIK can be rented with or without prepayment. The CLOUDBRIK T3 also comes with a pay-as-you-go option